You may be spending millions on server-side protections for your ecommerce site, but if you still think that your infrastructure “back door” is what malware developers are targeting, you’re likely losing significant site traffic to Client-Side Injected Malware (CSIM) – a new form of malware that attacks through your customer’s front door and is only gaining prominence in the malware community.
Most CMOs, CTOs and Heads of E-commerce are unaware of CSIM. It’s a field that has been growing rapidly in the past several years, with a notable spike in just the past six months. CSIM includes widgets (product recommendations and deals), advertisements and spyware scripts that are injected into websites, oftentimes looking like legitimate overlaid advertisements, or ‘injected ads’. Consumers typically download CSIM without realising it, either through bundled apps or malicious browser extensions. It’s become an exceedingly lucrative business for malware developers that use the naiveté of consumers to attack and drain revenue from brands and site publishers.
You might think your site looks one way, but consumers with CSIM infected devices – computer or mobile - see something entirely different (red outline added):
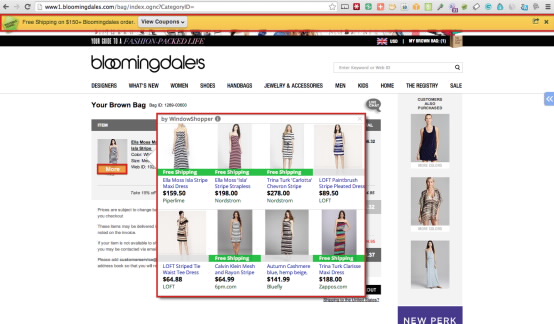
CSIM is injected through a layer that appears on top of your website once your site finishes loading on the consumer’s browser. It not only distorts the look of the web page, but also distorts your data and analytics. Once infected with CSIM, visitors will have a very different viewing experience than what you intended. Injected ads and malicious links will deform the webpage, often carefully enough to fool less savvy customers into clicking on malicious links that look legitimate, yet odd enough to deter more discerning viewers who will bounce off the page. Your customers are distracted and can easily become direct targets for phishing and other privacy infringement widgets.
Metrics and tools like heats maps will also be affected, as visitors are clicking on a layer of the website that is invisible to you. If you buy media per impression on a publisher’s website, an infected visitor won’t really see your ad, but you’ll be paying for it as if they did.
As CSIM is evolving, so are infection rates. Keep in mind it’s not your site that is infected but rather your visitor’s device, and CSIM rears it’s head more often when consumers visit sites with high average order values in industries including travel, luxury, and B2B ecommerce. We’ve found that content publishing and financial sectors are also highly targeted.
Working with top EU and US websites, our research has found that on average 15%-30% of visitors are infected with CSIM, skewing closer to 30% in travel, and hovering at 15% for financial institutions.
We’ve also seen a dramatic spike in iOS infection rates by 400% in the past six months alone. It’s clear that malware developers see the growing opportunity in mobile devices, and are taking advantage of the erroneous belief that Macs, iPads and iPhones are relatively impenetrable to malware as compared to their counterparts.
Watch out for the warning signs that visitors to your site are infected, especially on the media buying and ROI front. In our recent travel industry research, where the average CPC for travel-related keywords is 0.86$, we found that 11% of each CPC dollar is lost to CSIM. Considering travel advertising totaled $750M in 2013, that’s a whole lot of marketing dollars being tossed away.
Bounce rates, when coupled with declining sales/conversion rates, can be another obvious clue. One without the other can point to numerous issues, but when your marketing funnel is healthy yet site traffic isn’t converting, CSIM is likely the problem. We’ve identified over 25k injectors’ signatures affecting the user experience, with an average of more than 200 new injectors’ signatures being added to the mix daily. Don’t underestimate the problem – CSIM can undermine all of the money you spend on branding, and at the same time hide in plain sight.
True, this is a new frontier that we’re dealing with, but more and more major brands are getting wise to the topic. With so much revenue at stake, it isn’t surprising.
Until now, the burden allocation was clear – websites take care of their servers with firewall protections and massive IT teams, while consumers are expected to defend themselves against increasingly sophisticated malware with weak, and often dubious anti-malware tools available in the market. But, times have changed and brands are having to take matters into their own hands. If you truly want to control the customer experience, CSIM has to be your first priority.
By Chemi Katz, co-founder and CEO of Namogoo.
PrivSec Conferences will bring together leading speakers and experts from privacy and security to deliver compelling content via solo presentations, panel discussions, debates, roundtables and workshops.
For more information on upcoming events, visit the website.
comments powered by Disqus
